What is a DMARC record?
A DMARC record is the record where the DMARC rulesets are defined. This record informs the ISPs (like Gmail, Microsoft, Yahoo! etc.) if a domain is set up to use DMARC. The DMARC record contains the policy. The DMARC record should be placed in your DNS. The TXT record name should be “_dmarc.yourdomain.com.” where “yourdomain.com” is replaced with your actual domain name (or subdomain).
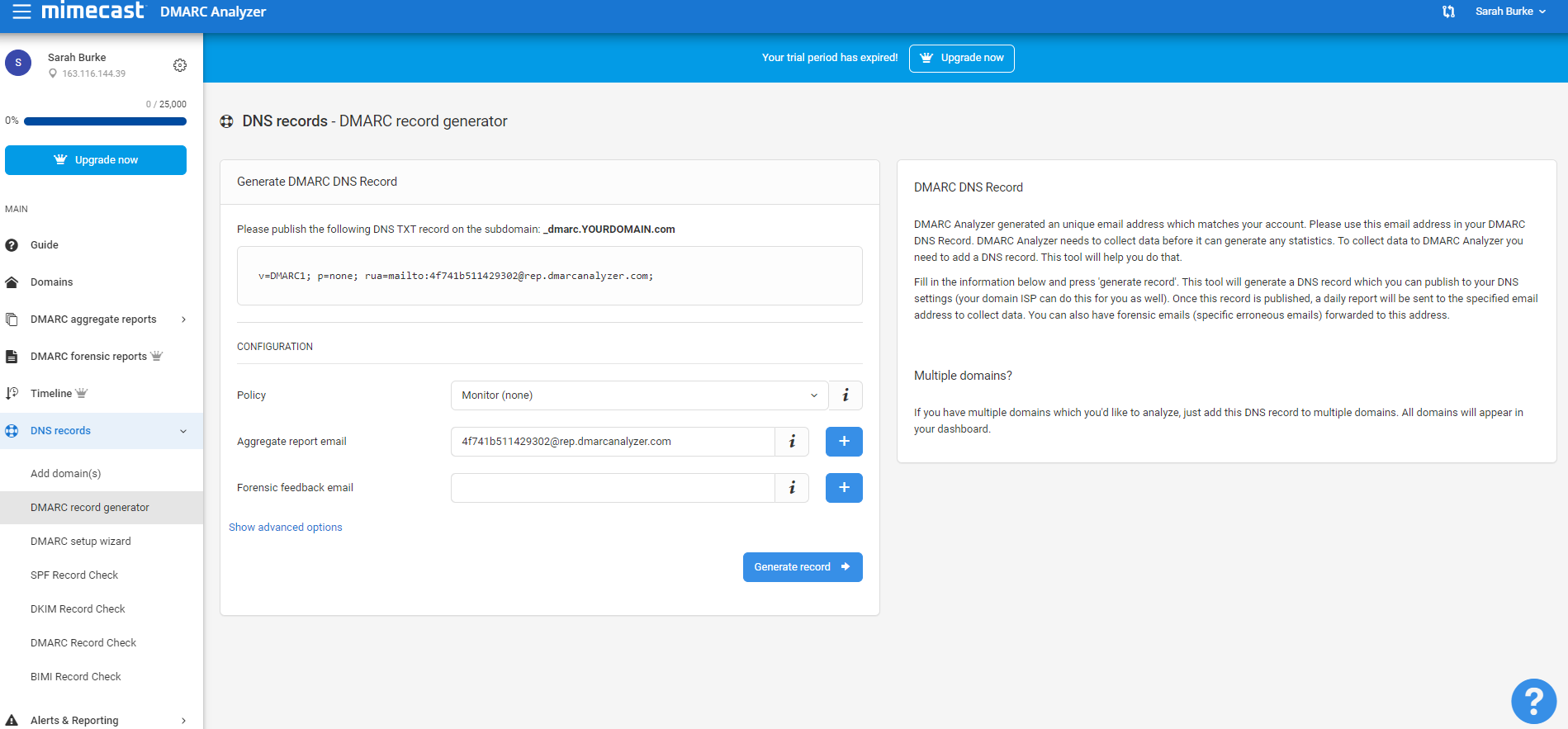
DMARC Analyzer helps you to get the DMARC record generation job done easily with our DMARC Record Generator. The free version of DMARC Analyzer allows you to use the DMARC Record Generator (sign up here). You can use DMARC Analyzer to generate an example DMARC record. Once SPF and DKIM are in place, you configure DMARC by adding policies to your domain’s DNS records in the form of TXT records (just like with SPF or DKIM).
The TXT record name should be “_dmarc.yourdomain.com.” where “yourdomain.com” is replaced with your actual domain name (or subdomain).
Common tags used in DMARC TXT records:
| Tag Name | Required | Purpose | Sample |
|---|---|---|---|
| v | required | Protocol version | v=DMARC1 |
| p | required | Policy for domain | p=quarantine |
| pct | optional | % of messages subjected to filtering | pct=20 |
| rua | optional | Reporting URI of aggregate reports | rua=mailto:CUSTOMERID@for.dmarcanalyzer.com |
| ruf | optional | Addresses to which message-specific forensic information is to be reported (comma-separated plain-text list of URIs). | ruf=mailto:CUSTOMERID@for.dmarcanalyzer.com |
| rf | optional | Format to be used for message-specific forensic information reports (comma-separated plain-text list of values). | rf=afrf |
| aspf | optional | Alignment mode for SPF | aspf=r |
| adkim | optional | Alignment mode for DKIM | adkim=r |
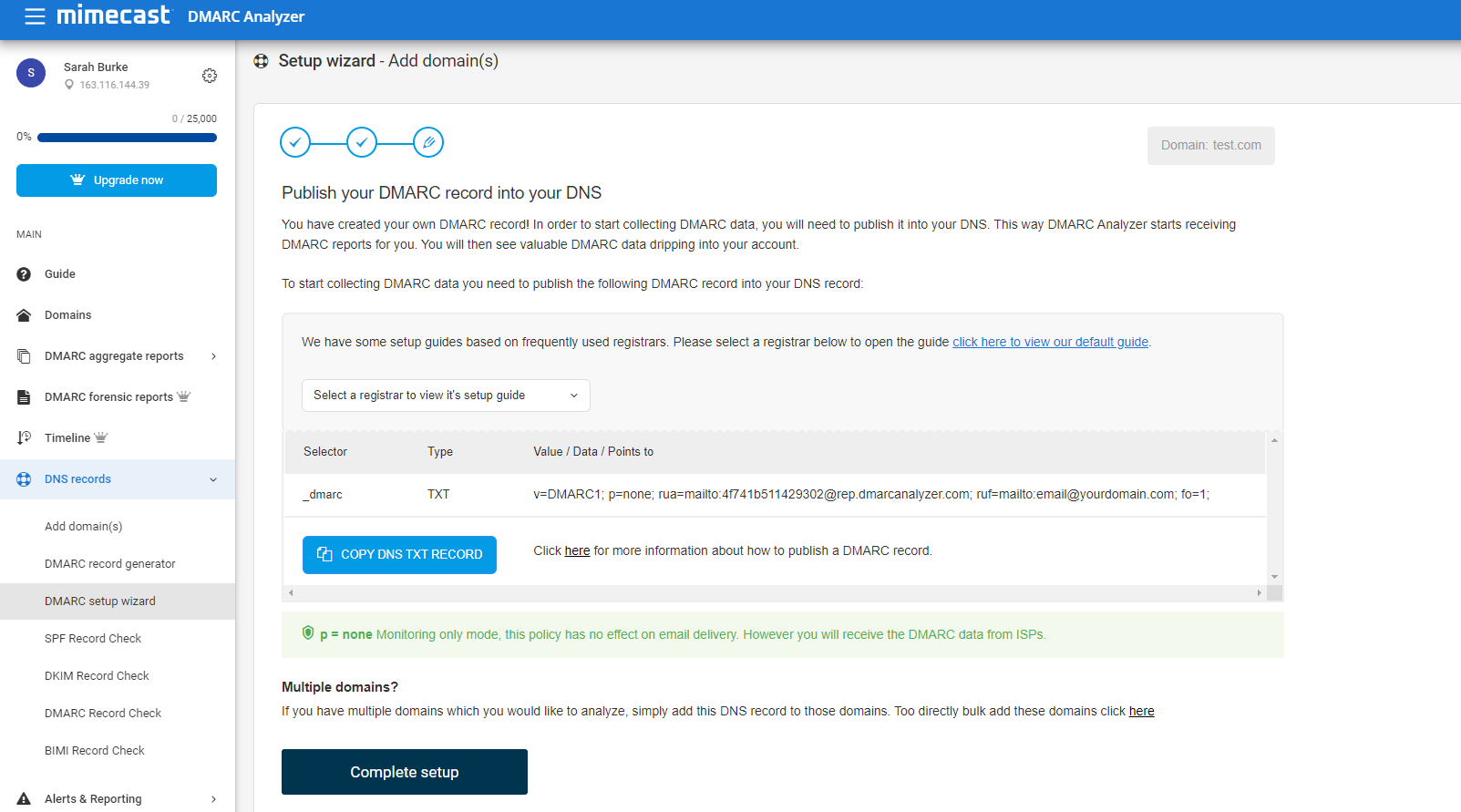
Visit DMARC Tag Registry for other available tags. When you log in on app.dmarcanalyzer.com go to “DNS Records” to generate your DMARC record. Only the v (version) and p (policy) tags are required.
Available DMARC policies
Three possible policy settings, or message dispositions, are available:
- none policy: You just want to monitor the DMARC results and you do not want to take specific action on all the failing emails. You can use the “none” policy to start with DMARC and gather all DMARC reports and start analyzing this data.
- quarantine policy: You put the emails which fail the checks in quarantine. Most of these emails will end up in the junk folder of the receiver.
- reject policy: You can reject all emails that fail the DMARC check. The email receivers should do this ‘on SMTP level’. The emails will bounce directly in the sending process.
Choose one of the three DMARC policies to define how you want the email receivers to handle emails which fail the DMARC checks of your DMARC record.
Alignment mode (aspf / adkim) refers to the precision with which sender records are compared to SPF and DKIM signatures, with the two possible values being relaxed or strict. represented by “r” and “s” respectively. In short, relaxed allows partial matches, such as subdomains of a given domain, while strict requires an exact match.
Make sure to include your email address with the optional rua tag to receive the daily reports. If you want to use DMARC Analyzer to analyze your reports, make sure to use the DNS record generation tool to get the aggregate- and forensic feedback e-mail addresses.
Creating a TXT record with the appropriate name and value is different for every domain host. Contact us if you need help setting it up with your provider.
It should be rather simple and may look something like this in the generator:
| Use the DMARC Record Generator to create your own DMARC record |
| Use the DMARC Record Checker to display, test and verify your DMARC record whether it’s valid |
| Use the record setup guides for guidance on how to set up your DMARC record for specific webhosts |
| User friendly DMARC analyzing software |
Example DMARC report
The daily reports come in an XML format. Read them to better understand your mail flow. The reports help you ensure your outbound mail sources are authenticating properly. Ensure that the various IPs sending email claiming to come from your domain are indeed legitimate, configure them properly with DKIM or add them to their SPF range. The reports also help administrators take fast action when they have a block policy in place if a new mail source comes online or an existing email source’s configuration breaks.
Here is an excerpt of a report showing results for messages sent from a couple of IP addresses, one sent directly and the other forwarded. Both messages passed:
<record>
<row>
<source_ip>207.126.144.129</source_ip>
<count>1</count>
<policy_evaluated>
<disposition>none</disposition>
</policy_evaluated>
</row>
<identities>
<header_from>yourdomain.com</header_from>
</identities>
<auth_results>
<dkim>
<domain>yourdomain.com</domain>
<result>pass</result>
<human_result></human_result>
</dkim>
<spf>
<domain>yourdomain.com</domain>
<result>pass</result>
</spf>
</auth_results>
</record>
<record>
<row>
<source_ip>207.126.144.131</source_ip>
<count>1</count>
<policy_evaluated>
<disposition>none</disposition>
<reason>
<type>forwarded</type>
<comment></comment>
</reason>
</policy_evaluated>
</row>
<identities>
<header_from>yourdomain.com</header_from>
</identities>
<auth_results>
<dkim>
<domain>yourdomain.com</domain>
<result>pass</result>
<human_result></human_result>
</dkim>
<spf>
<domain>yourdomain.com</domain>
<result>pass</result>
</spf>
</auth_results>
</record>
Deploy your DMARC policy slowly
We strongly recommend ramping up DMARC use slowly by employing these policies in this order. First, monitor your traffic and look for anomalies in the reports, such as messages that are not yet being signed or are perhaps being spoofed. Then, when you’re comfortable with the results, change the TXT record policy setting from “none” to “quarantine.” Once again, review the results, this time in both your spam catch and in the daily DMARC reports. Finally, once you’re absolutely sure that all of your messages are signed, change the policy setting to “reject” to make full use of DMARC. Revisit reports to ensure your results are acceptable.
Similarly, the optional pct tag can be used to stage and sample your DMARC deployment. Since 100% is the default, passing “pct=20” in your DMARC TXT record results in one-fifth of all messages affected by the policy actually receiving the disposition instead of all of them. This setting is especially useful once you decide to quarantine and reject email. Start with a lower percentage to begin with and increase it every few days.
So, a conservative deployment cycle would resemble:
Attempt to remove the percentages to complete the deployment. As always, review your daily reports.
Want to create your own DMARC record?
| Use the DMARC Record Generator to create your own DMARC record |
Is my email flow configured correctly?
While implementing DMARC you will use the DMARC data to analyze your current email flows. You can do this by checking the data and verifying that your sending sources are configured correctly.
Please note that if you’re testing an updated DNS record (either DKIM or SPF), there could be DNS cache involved which influences the result. Updates to your SPF record should always be tested before performing them by using our prevalidation SPF checker.
User friendly DMARC analyzing software
DMARC Analyzer provides user friendly DMARC analyzing software and act as your expert guide to move you towards a reject policy as fast as possible. DMARC Analyzer provides a SaaS solution which empowers organizations to easily manage complex DMARC deployment. The solution provides 360° visibility and governance across all email channels. Everything is designed to make it as easy as possible.
| Use the DMARC Record Generator to create your own DMARC record |
| Use the DMARC Record Checker to display, test and verify your DMARC record whether it’s valid |
| Use the record setup guides for guidance on how to set up your DMARC record for specific webhosts |
| User friendly DMARC analyzing software |
DMARC Analyzer provides user friendly DMARC analyzing software and act as your expert guide to move you towards a reject policy as fast as possible.